In today’s complex digital landscape, managing operating system credentials is a critical cybersecurity cornerstone. This guide delivers an in-depth technical walkthrough for changing your Windows 11 password, exploring GUI and command-line methods, cryptographic principles, and modern identity management strategies tailored for IT professionals and power users.
Changing your Windows 11 password is a fundamental act of digital security hygiene. This process not only prevents unauthorized access but also mitigates risks like credential stuffing attacks if the same password was exposed elsewhere. In Windows 11, authentication data for local accounts is stored in an encrypted SAM (Security Account Manager) file. Updating your password generates a new cryptographic hash (typically using NTLM or bcrypt algorithms), which replaces the old entry in this secure database.
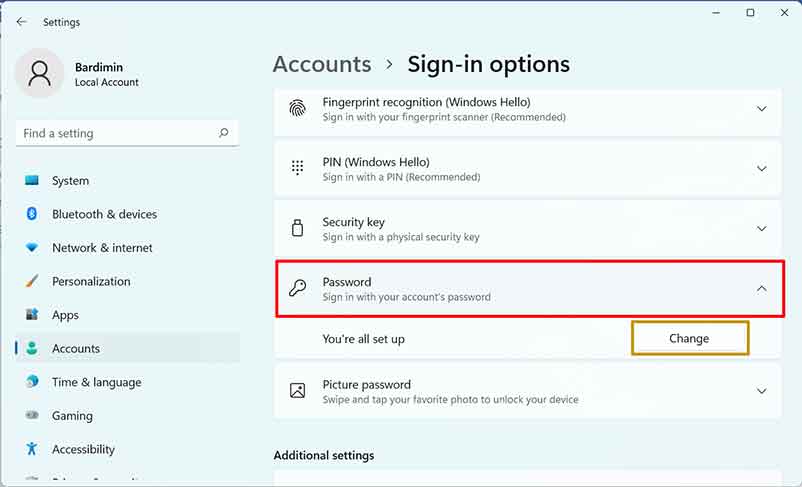
Method 1: Changing Your Password via the Settings Interface (GUI)
This is the standard, user-friendly procedure. The Settings app provides a guided workflow that validates input and immediatley updates the password hash in the system.
- Access Settings: Press
Windows + I. Navigate to Accounts > Sign-in options. Under the “Password” header, click the “Change” button. - Verify Your Identity: Enter your current password. This crucial step provides authentication proof, preventing unauthorized changes from a locked session.
- Create New Credentials: Type your new password in the “New password” and “Confirm password” fields. The system validates strength based on active Group Policy complexity rules. The optional “Password hint” field should not reveal the password itself.
- Finalize: Click “Finish“. The change is instant. You may need to re-authenticate at the lock screen for the new credentials to fully load.
Method 2: Using the Secure Security Screen (Ctrl + Alt + Del)
This alternative method runs in a high-security context. The menu accessed via Ctrl + Alt + Delete operates on a secure desktop, isolated from most user processes and common keyloggers.
- Press
Ctrl + Alt + Deletesimultaneously. - Select “Change a password“.
- Enter your old password, followed by the new one and its confirmation.
- Press
Enter. A “Your password has been changed” notification confirms success.
Technical Analysis: Secure Desktop Security
The Ctrl + Alt + Del key combination triggers a hardware interrupt handled directly by the Windows kernel. The kernel then switches to a secure attention sequence (SAS) and displays the secure desktop. This environment has a very high integrity level, ensuring user input cannot be intercepted or hooked by applications running on the regular user desktop. Thus, this method is advised in high-threat environments or when malware infection is suspected.
Method 3: Command-Line Tools for Technicians & Administrators
For automation, scripting, or remote management, using an elevated Command Prompt or Windows PowerShell is highly effective. These commands directly manipulate user entries in the system.
# Change password using PowerShell (Run as Administrator)
net user [username] [newpassword]Replace [username] with the target account name and [newpassword] with the new password. For better security, use the following cmdlet which accepts hidden input:
$NewPassword = Read-Host "Enter New Password" -AsSecureString
Set-LocalUser -Name "[username]" -Password $NewPasswordImportant Note: This method requires administrative privileges. Without the -AsSecureString parameter, the password may be recorded in plaintext within command history. Always audit command history after execution.
Cryptographic Principles & Password Security Best Practices
Changing your Windows 11 password should be paired with strong password principles. Windows typically uses NTLMv2 or bcrypt hashing, which resists rainbow table attacks, but weak passwords remain vulnerable to offline brute-force if the SAM file is compromised.
- Complexity and Lenght: Use a passphrase of at least 14 characters mixing cases, numbers, and symbols. Example:
M4kaN#B1sni$T4hun2024is far stronger thanpassword123. - Uniqueness: Never reuse a password from other services (email, social media) for your Windows local account.
- Consider Passwordless Authentication: For superior security, leverage Windows Hello (biometrics) or a FIDO2 security key. These use public-key cryptography and are more resistant to phishing than static passwords.
- Secure Management: Use a trusted password manager to generate and store complex passwords. Avoid writing them down in plaintext documents.
Troubleshooting and Special Scenarios
If you forget your current local account password, the process becomes more complex due to security design.
- Using a Password Reset Disk: If you created one beforehand (via Control Panel > User Accounts), use it at the login screen to set a new password without the old one.
- Via Another Administrator Account: Log in with a different admin account, go to
Control Panel > User Accounts, manage another user, and select “Change the password”. This bypasses the need for the old password. - Using Windows Installation Media: In worst-case scenarios, technicians can use installation media to access a pre-boot Command Prompt and reset passwords using tools like
utilman.exeor direct SAM manipulation. This requires deep technical expertise and may violate organizational policy.
Conclusion
Understanding the multifaceted approch to changing your Windows 11 password is an essential skill. From standard graphical methods to command-line automation, each approach has its specific use case and security implications. Always prioritize strong, unique passwords and consider adopting modern authentication like Windows Hello to significantly enhance your overall security posture. Implementing these measures solidifies the first line of defense for your operating system.


