SoftPerfect File Access Monitor is a versatile application for monitoring file access and offering a complete history of anyone who read, wrote, and manipulated it.
SoftPerfect File Access Monitor can be used on file servers to monitor network user activity and on local computers to monitor local user file access. It’s comparable to Windows’ auditing features basically, but it’s easier to use and offers configurable reporting and alerting capabilities.
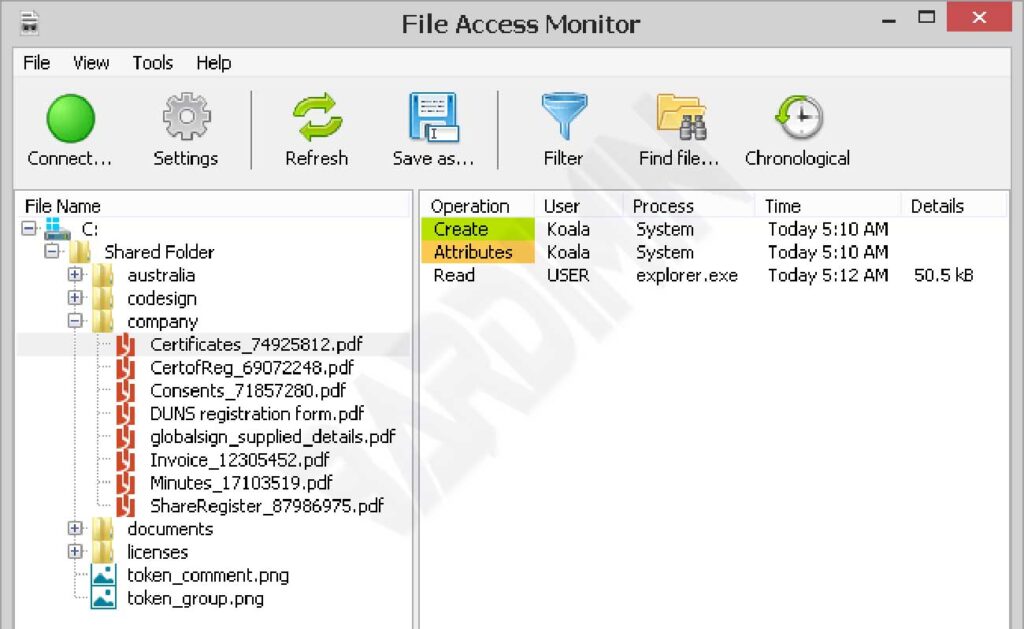
SoftPerfect File Access Monitor comprises two parts: the File Monitoring Service, which maintains tracking of accessed files, and the Management Console, which is used for setup and monitoring.
When you open the Management Console, you will be prompted to enter the host name and password for the File Monitoring Service. The host name is set to localhost by default, and the password is left blank. To access a service that you installed on another computer, enter its IP address or name.
SoftPerfect Features
- Monitor file actions: create, move, delete, read, and write to files.
- Record remote user access to a shared folder.
- Track local users about what files they are accessing.
- Displays a powerful filter system to include or exclude specific activities.
- Standalone does not require a shared database server.
Supported Operating Systems
- Windows XP to Windows 10,
- Windows Server 2003 through 2012
