Asterisk Password Spy is an app to show hidden passwords by using an asterisk (****).
For security issues, most programs only display an asterisk (****) in place of the actual password. However, often you need to know the real pass phrase, especially if you forget the password you have created.
The application has an easy-to-use User Interface. Just by dragging the “search symbol” to the password box, you can easily reveal the real password.
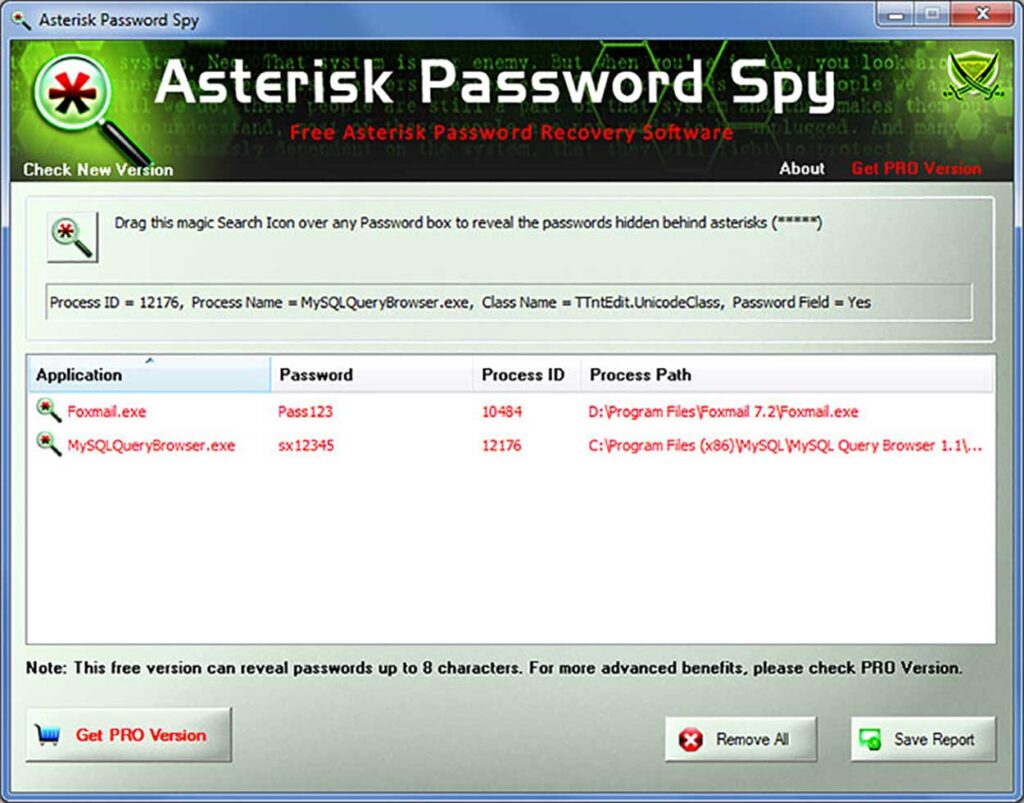
Asterisk Password Spy will allow you to quickly uncover passwords hidden by asterisks.
Other Interesting Articles
Features of Asterisk Password Spy
- Immediately reveal the password hidden behind the asterisk.
- Supports most windows-based applications.
- The easier user-friendly GUI interface makes it quick to use.
- Sort features to set up and search quickly through found passwords.
- Save the list of recovered passwords to an HTML/XML/CSV file.
- Support for local installation and software uninstallation.
Limitations of Asterisk Password Spy
- It doesn’t work with non-windows-based applications such as GTK, Flash, QT, or applications that do not use the standard edit box for passwords.
- Does not work with HTML pages in browsers like IE, Firefox, Chrome, etc.
- Nor will it work with apps where the password doesn’t exist. Several times, the application does not enter the password in the password box to hide from this tool.
