Kaizala is a chat application that is quite famous and is a product of Microsoft. With the big-name Microsoft, of course, the quality and security of Kaizala do not need to be in doubt.
As a chat application, Kaizala is still less popular than WhatsApp. Organizations or companies widely used Kaizala because it has an attendance feature.
This attendance request feature has an option that requires you to mark attendance and send the address where you are located and can also be accompanied by a photo. Then the admin of a group will download the results of the attendance.
What if you don’t want to provide your location?
Attendance requests on Kaizala require you to provide a location address. If you turn off GPS on your smartphone device, you cannot mark the attendance request.
To solve this problem, you can use a fake location by using a GPS application that is widely available on the Playstore.
Can you find out if you use a fake location?
The admin of the group can tell if you are using a fake GPS application. The coordinates of the fake GPS have a different number of digits than the real GPS. The original GPS coordinates have an average numerical scale of 5-7 digits (-5.3289161). While the fake GPS application has a numerical scale of over 12 digits (-5.32903405631405).
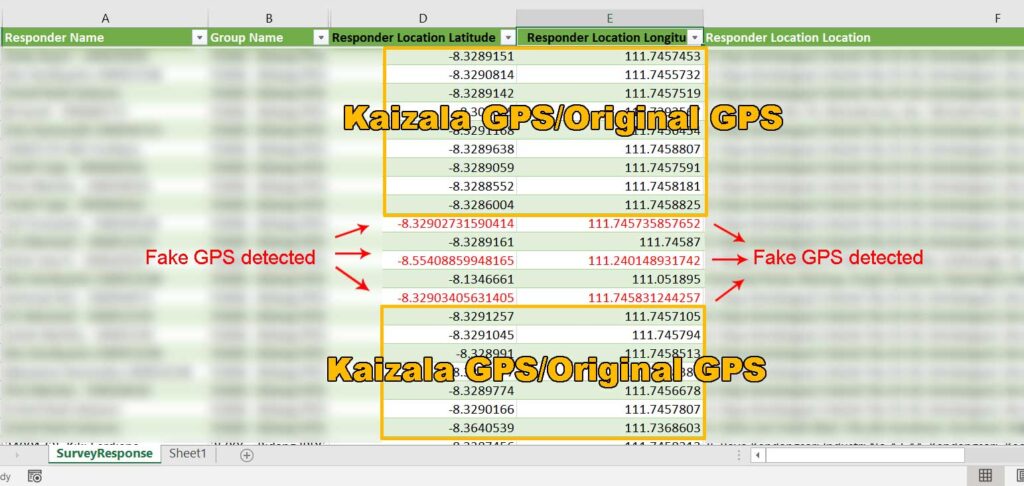
Kaizala Attendance Hacking
So that you are not known if you use a fake GPS application when marking attendance requests on the Kaizala application, you must use a fake GPS application that produces coordinates with the number of digits as in the original.
One of the fake GPS applications that can do this is the ” KAIZALA GPS ” application “. You can download the application through the Playstore or via the following link. Download Kaizala GPS.

