HTTP Toolkit is an open-source tool for debugging, testing, and creation using HTTP(S).
The HTTP Toolkit application allows you to intercept, inspect, and rewrite HTTP(S) communications from anywhere. Check traffic from your browser, microservices, and Android apps to debug, understand, and test anything.
The HTTP Toolkit offers you direct access to and insight into every request and response. Quickly test the client, troubleshoot API issues, and find errors.
With its ability to support normal HTTP queries from any language or tool, the HTTP Toolkit should serve as an HTTP(S) proxy for platforms that do not have automatic integration.
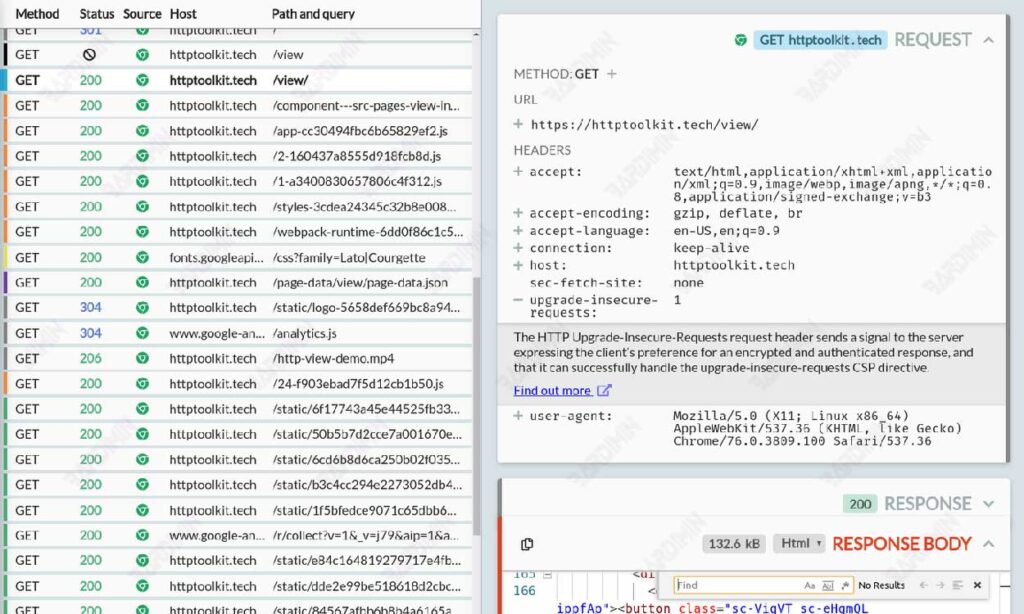
You can quickly scan traffic using the HTTP Toolkit by highlighting the content type, status, and source or by performing a search using URLs, statuses, and headers to find important messages.
After successfully capturing HTTP client traffic, you can investigate & analyze it. It can be a great tool for troubleshooting and often helps in understanding how the application acts and communicates.
After successfully intercepting HTTP client traffic, the HTTP Toolkit allows you to manually and automatically replicate and rewrite intercepted HTTP requests and answers.
Key Features of HTTP Toolkit
- With a one-click setup, instantly intercept browsers, most backend languages & scripts (from Node.js to PHP), Android devices, Electron apps, and more.
- Collect useful traffic without filtering everything on your device, so there are only things you care about and no unwanted noise or adverse effects.
- Check the entire header and body of each request and response from each client to see exactly what is being sent and received over the wires.
- With built-in documentation for all general headers and response states, as well as body decoding, highlighting, folding, and other minutiae, driven by the same internals as the Visual Studio Code, it’s easy to understand the HTTP data collected.
- With client-highlighted exchanges, category-tagged tags (such as images, JSON replies, and errors), and text filtering & freely structured across all request & response data, you can find the information you need quickly.
- A breakpoint direct request or answer to dynamically rewrite HTTP traffic.
- A configurable dummy endpoint or server with customizable rule settings to automatically match and process requests, send replies, enter errors and timeouts, or transparently reroute requests to other destinations
- With the HTTP Toolkit, a transparent HTTP proxy, you can intercept any HTTP traffic on a single port, including plain HTTP, encrypted HTTPS traffic, WebSockets communication, HTTP/2 traffic, proxy requests, direct requests, manually redirected packets, and more.
Supported operating systems
HTTP Toolkit is available for Windows, Mac & Linux.
