Ethical and Legal Advisory: This content is compiled for the educational purpose of IT technicians and professionals conducting in-depth software evaluation. Using tools to permanently avoid licensing payments infringes on intellectual property rights. Always support software developers by purchasing official licenses for commercial or long-term use.
Paid software trial periods are often limited to 30 days, which may be insufficient for thorough evaluation in complex technical environments. This technical article provides an in-depth analysis of three methodologies to extend software trial periods: process time manipulation, registry trace cleaning, and system call hooking. We review the working principles, implementation scenarios, and security implications of RunAsDate, Trial-Reset, and Time Stopper tools for IT audit and professional QA needs.
Software Trial Protection Architecture and Evaluation Methods
Before discussing specific tools, it’s crucial to understand the mechanisms used by paid software to protect trial periods. Implementations are generally divided into three layers. The first layer is registry-based storage, where installation date and day-X information are stored in the HKEY_CURRENT_USER\Software or HKEY_LOCAL_MACHINE keys. The second layer involves hidden marker files placed in system folders or AppData. The third and most complex layer is online validation against vendor servers, although this is rare during trial phases.
Therefore, the approach to extending trial usage must be tailored to these protection layers. Legitimate evaluation methods are required when technical teams need to test software integration with internal systems, compatibility with specific hardware, or performance under high workloads that require more time than the standard trial limit.
1. RunAsDate: Intercepting GetSystemTime and GetLocalTime APIs
RunAsDate from NirSoft operates at the application programming interface (API) level. This tool uses DLL injection techniques to inject code into the target process’s memory space. This code then hooks system functions responsible for retrieving time, such as GetSystemTime, GetLocalTime, and GetSystemTimeAsFileTime. Whenever the target application calls these functions, the returned value is the user-configured time, not the actual system time.
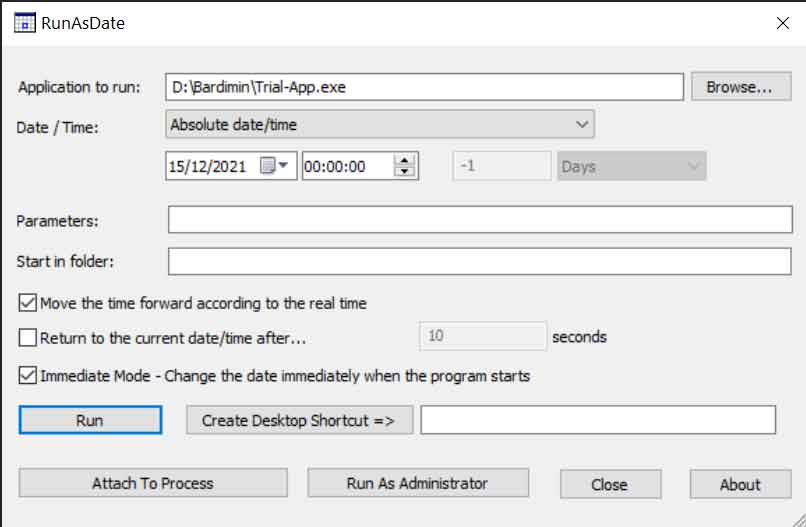
Technical usage scheme: This utility is highly effective for software that performs on-the-fly time checks during execution. For 64-bit software, use RunAsDate64.exe. Time parameters can be set via command line for testing script automation. Its weakness is ineffectiveness against software that stores encrypted timestamps in configuration files or validates with background services. Additionally, some Endpoint Detection and Response (EDR) security solutions may identify this DLL injection technique as suspicious activity.
2. Trial-Reset 4.0: Forensic Registry and Scatter Files Analysis
Unlike the runtime approach, Trial-Reset adopts a post-uninstall strategy. This tool functions as a scanner and cleaner of digital trial traces. Its algorithm not only searches for vendor name patterns in the registry but also performs signature analysis on system files to identify scatter files—small marker files left behind by the uninstall process.
Recommended operational procedure: 1. Create a registry snapshot and monitor file activity with tools like Process Monitor (Microsoft Sysinternals) during trial software installation. 2. Identify written registry keys and file locations. 3. After the trial period expires, use Trial-Reset to clean all identified traces. 4. Perform reinstallation. The software will behave like a first-time installation.
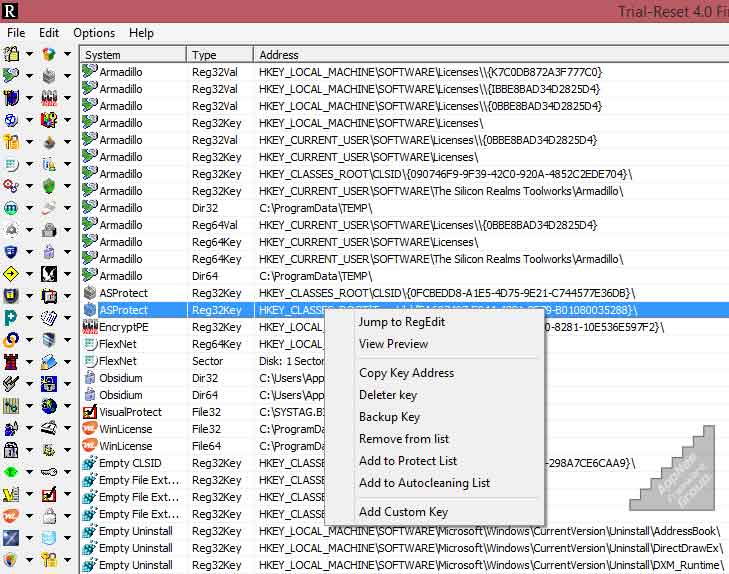
The main risk is deletion of shared registry keys used by other applications. Therefore, always create a registry backup (reg export) before running cleanup. Newer versions of protection software like FlexNet Publisher or Sentinel HASP now use kernel drivers to store status, making user-mode cleanup methods increasingly less effective.
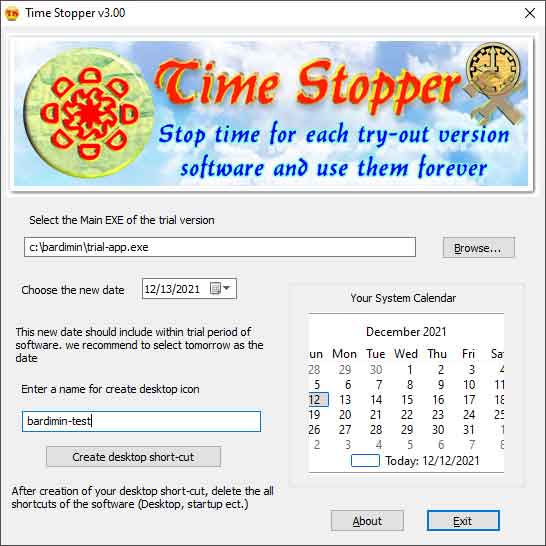
3. Time Stopper: Kernel-Level Hooking and Time Virtualization
Time Stopper evolves from the RunAsDate concept with deeper scope. Some variants of this tool attempt to operate at the kernel level through unsigned drivers. These drivers hook the KeQuerySystemTime function or interrupt the System Time Clock (STC) for specific processes. This approach is more aggressive and poses risks to system stability, but is harder to detect by protection software running in user mode.
In practice, such tools are often used by gamers to manipulate time in single-player games with time-based content. However, in a professional context, similar utilities can be leveraged to “freeze” software state during stress testing or debugging requiring static time conditions.
Cybersecurity Risk Analysis and Mitigation
Downloading and executing system modification tools from unofficial sources carries significant dangers. Many repacked distributions contain Trojans, coin miners, or spyware. Specific risks include:
- Credential Theft: Keyloggers can be embedded in tool installers.
- Backdoor Installation: Opens doors for unauthorized remote access.
- System Instability: Poor kernel hooks can cause Blue Screen of Death (BSOD).
Mitigation steps for professionals: 1. Use isolated environments (virtual machines or dedicated machines) for testing. 2. Analyze file hashes (MD5, SHA-256) and compare with values from official sources. 3. Perform static analysis with tools like PEiD or Detect It Easy to identify suspicious packers. 4. Monitor network and system activity with Wireshark and Process Explorer during use.
Conclusion and Best Practices for Technical Evaluation
Extending software trial periods is an action justifiable only within the scope of legitimate, time-limited technical evaluation. A deep understanding of protection mechanisms, selecting the appropriate tool based on the target software’s architecture, and execution in a secure environment are mandatory.
More ethical and legal alternatives include utilizing extended evaluation programs offered by many vendors for corporate customers or partners. Furthermore, requesting temporary license keys (NFR/evaluation keys) directly from vendors for proof-of-concept projects is often the best option. Thus, system integrity is maintained, and software developers receive due support for their innovations.


