Steps to Identify Malware Processes Using Process Explorer
- Run Process Explorer on your Windows 11 system.
- Notice the processes marked in purple in the list of processes. Purple-colored processes are most likely malware because the files are compressed or packaged, which can hide malicious code.
- Right-click on the suspicious process and select “Properties” to check for more information.
- Check if the process is running under an unusual user account, such as not NT AUTHORITY\SYSTEM, LOCAL SERVICE, or NETWORK SERVICE. Processes running under other accounts are likely malware.
- If the process is an instance of svchost.exe, right-click and check its properties. The native Windows process will start with C:\Windows\System32\svchost.exe –k. If not, it might be malware.
Color Coding Process in Process Explorer
Process Explorer uses color coding to help users identify the type of process that is running. The following is an explanation of the color coding used:
Purple Process:
Indicates a compressed file (also known as packaged), which can hide malware code. This process is often an early indication of malware, as they are designed to hide themselves from antivirus scanners.
Red Process:
Indicates the process that is being stopped. This means that the process has been shut down or is in the process of being terminated.
Green Process:
Indicates a process that has just been carried out (also known as being born). This process may have just been launched and needs to be further checked to ensure its security.
Light Blue Process:
Shows the process run by the same account that started Process Explorer. This helps users understand the context in which the process is coming from.
Dark Blue Process:
Shows the process currently selected by the user in the Process Explorer view. This makes it easier for users to focus on specific processes.
Pink Process:
Shows the services running on the PC, including critical system processes such as svchost.exe. This process can accommodate one or more other services, sharing resources for efficiency.
Using Color Encoding for Malware Identification
By understanding this color coding, users can quickly identify potential threats in their systems. Purple-colored processes should be further examined to ensure that they are not malware, while other processes also need to be monitored based on their context and behavior.
Utilizing this feature in Process Explorer allows users to conduct an in-depth analysis of system activity and take necessary preventive measures to protect the computer from malicious threats.
Checking SVCHOST.EXE for Malware
Malware often tries to mimic the svchost.exe process because it is a critical component of the Windows operating system that runs system services. Since many users and security software recognize svchost.exe as a legitimate process, the malware takes advantage of this to hide its existence.
svchost.exe processes typically have many instances running in the background, making it more difficult to detect unauthorized processes. Malware disguised as svchost.exe can evade detection by using a similar name or by operating under unusual user accounts.
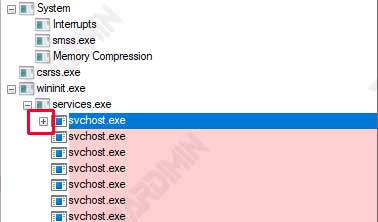
How to Use the [+] Icon to the Left of a Process to See Subprocesses That May Be Malware
- Run the Process Explorer app on your computer.
- Search the list of processes and find all instances of svchost.exe. You will see several entries for this process.
- To the left of the svchost.exe process name, you’ll see the [+] icon. This icon indicates that the process has subprocesses that can be further examined.
- Click on the [+] icon to expand the view and see the subprocesses associated with that svchost.exe instance. It will display all the subprocesses that may potentially be malware.
- Check those subprocesses to see if anything is suspicious or unknown. If you find a subprocess with an unusual or unfamiliar name, this could be an indication of malware.